Google Cloud Platform (GCP) is one of the leading cloud computing platforms, providing a wide range of services for businesses to build, deploy, and manage their applications and infrastructure in the cloud. However, with the increasing number of cyber threats and regulations related to data protection and privacy, security, and compliance are becoming major concerns for companies using cloud services.
In this article, we will discuss the features of GCP and how it can help you protect your data and comply with regulations.
The Importance of Security in Cloud Computing for Businesses
The importance of security in cloud computing for businesses cannot be overstated. As more companies move their applications and infrastructure to the cloud, the risk of cyber threats and data breaches increases. Cloud environments are attractive targets for attackers because they contain large amounts of sensitive data and are accessible from anywhere in the world.
Companies also face compliance regulations related to data protection and privacy. Failure to comply with these regulations can result in significant fines and damage to a company’s reputation. Therefore, businesses must ensure that their cloud infrastructure is secure and compliant.
Implementing strong security measures in the cloud can help protect your data, mitigate risk, and ensure compliance. This includes securing your cloud environment, encrypting sensitive data, monitoring user activity, and implementing access controls. By taking a proactive approach to cloud security, businesses can safeguard their data, money, and reputation, and focus on achieving their business objectives.
Why GCP Is a Good Option for Security and Compliance
Google GCP Cloud has built-in security features that help businesses protect their data and systems. These features include data encryption at rest and in transit, access controls, and advanced threat detection tools. Google GCP Cloud also provides compliance certifications and attestations, which demonstrate that their services meet rigorous standards.
Moreover, GCP provides a range of tools and services that enable businesses to monitor and manage security risks across their entire cloud infrastructure. These tools include a comprehensive security center, auditing frameworks, and vulnerability management tools. This means that businesses can proactively identify and address security risks before they become major issues.
Below we will see some of the strengths of Google’s cloud services that can be a differential that can lean the decision when hiring a cloud provider:
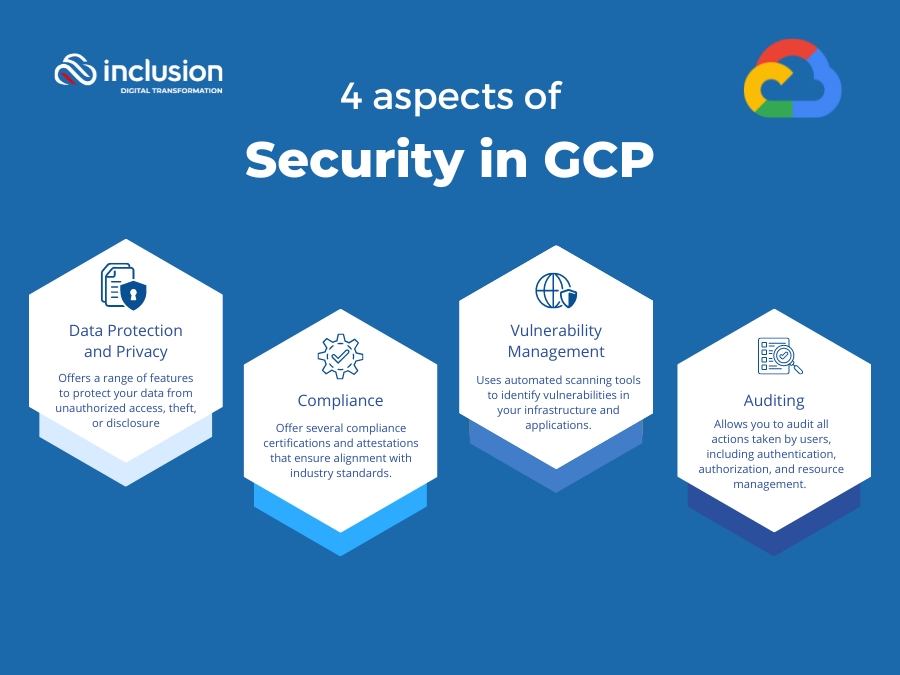
Data Protection and Privacy
Data protection and privacy are critical aspects of any cloud computing platform, and GCP offers a range of features to protect your data from unauthorized access, theft, or disclosure. These features include encryption, data access controls, and data segregation.
Encryption is a process of converting plain text into cipher text that can be read only by authorized users. GCP provides several encryption options, including server-side encryption for data at rest and client-side encryption for data in transit. Additionally, GCP uses Google’s hardware security modules (HSMs) to provide industry-standard encryption for all data stored in the cloud.
Data access controls are used to restrict access to data based on user roles and permissions. GCP provides identity and access management (IAM) that allows you to manage access to resources based on user roles and permissions. You can define roles and permissions for users, groups, and service accounts and restrict access to sensitive data based on the principle of least privilege.
Data segregation is the process of separating data from different customers on the same physical infrastructure to prevent data leakage or unauthorized access. GCP provides multi-tenancy support that ensures that each customer’s data is kept separate and secure.
Compliance
Compliance is another important part of cloud computing, especially for companies that are subject to industry regulations such as HIPAA, GDPR, or PCI DSS.
GCP can offer several compliance certifications and attestations that ensure that your data is stored, processed, and transmitted in compliance with industry standards.
Vulnerability Management
Vulnerability management is the process of identifying and remediating vulnerabilities in software or hardware systems to prevent cyber-attacks or data breaches.
GCP uses automated scanning tools to identify vulnerabilities in your infrastructure and applications. These tools scan your systems for known vulnerabilities and provide you with actionable insights to remediate them.
Google also provides a comprehensive security center that allows you to monitor and manage security risks across your entire cloud infrastructure. You can track security events, view security recommendations, and use advanced threat detection tools to detect and respond to security threats in real-time.
Auditing
Auditing is the process of recording and analyzing system events and activities to identify security breaches, policy violations, or operational issues. GCP assists companies with a comprehensive auditing framework that enables them to monitor and analyze all activities in their cloud infrastructure.
GCP allows you to audit all actions taken by users, including authentication, authorization, and resource management. You can use audit logs to track changes to your infrastructure, monitor access to sensitive data, and investigate security incidents.
Conclusion
Google Cloud Platform is a robust cloud computing service that offers amazing results for businesses to build, deploy, and manage their applications and infrastructure. However, with the increasing number of cyber threats and regulations related to data protection and privacy, security, and compliance are becoming a top priority for companies throughout the digital transformation journey.
If you are looking to migrate to the cloud or need help managing your cloud infrastructure, contact us today. Our experts can help you design, deploy, and manage your IT infrastructure, ensuring that your data is protected, and your systems are secure and compliant.